
APIs are everywhere and API knowledge is becoming increasingly important in various roles, not just for developers. According to Postman’s 2023 State of the API Report, 53% of people who work with APIs are non-developers. This indicates that API knowledge is relevant for a wide range of positions, including product managers, data analysts, and customer success managers.
Additionally, job descriptions are increasingly listing “knowledge of REST APIs” as a requirement, even for non-developer roles. This trend suggests that API knowledge is becoming more prevalent in job interviews across different fields, though an exact percentage is not provided.
Here are top 10 interview questions you need to be prepared for when asked about APIs :
1.What is API?
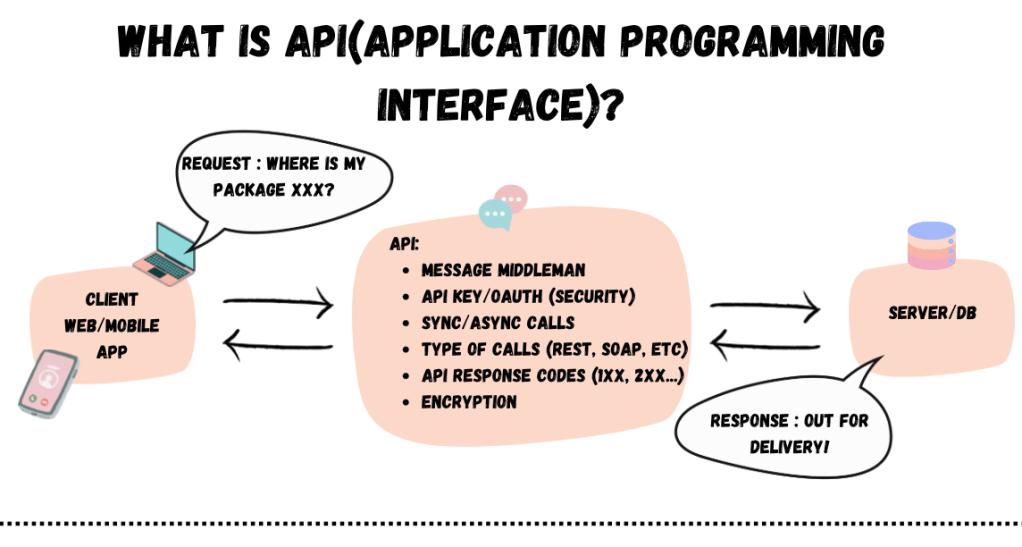
By definition, an API, or Application Programming Interface, is a set of protocols, routines, and tools that enable different software applications to communicate with each other. It acts as an intermediary, allowing one program to request data or functionality from another program and receive a response.
In layman’s terms, it is a communication protocol to send/request data and receive a response/acknowledgement. It is truly a mediator/ middle man to send messages between two systems.
2.How does an API work?
APIs work through a request-response cycle:
- A client (such as a mobile app or website) sends a request to the API.
- The API processes the request and communicates with the server or database.
- The server sends a response back through the API.
- The API delivers the response to the client.

3. What are the Major benefits of API?
This process enables various applications to share data and functionality without needing to share their entire codebase. APIs are crucial in modern software development for several reasons:
- simplify code and improve efficiency.
- enable faster development of complex functionality.
- allow for seamless integration between different systems and services.
4. What are the Common types of web APIs?
1. REST APIs(MOST POPULAR)
Representational State Transfer (REST) APIs are one of the most widely used types of APIs. They use standard HTTP methods like GET, POST, PUT, and DELETE to interact with web services. REST APIs are known for their simplicity, scalability, and stateless nature.
Benefits of REST APIs:
- Easy to implement and widely adopted.
- Support multiple data formats, including JSON and XML.
- Allow stateless communication, improving scalability.
2. SOAP APIs
Simple Object Access Protocol (SOAP) APIs use XML-based messaging protocols for communication. Unlike REST APIs, SOAP APIs are more rigid but provide enhanced security and reliability, making them ideal for financial and enterprise applications.
Benefits of SOAP APIs:
- higher security with built-in encryption and authentication.
- strict communication standards, making them reliable.
- for applications that require high levels of transactional integrity.
3. GraphQL APIs
GraphQL is a query language for APIs that allows clients to request specific data rather than receiving a predefined response. Developed by Facebook, GraphQL APIs provide more flexibility and efficiency compared to traditional REST APIs.
Benefits of GraphQL APIs:
- to request only the needed data, reducing over-fetching.
- high performance by enabling precise data retrieval.
4. gRPC (Google Remote Procedure Call)
gRPC is an open-source, high-performance remote procedure call (RPC) framework initially developed by Google. It enables efficient communication between distributed systems and services, allowing developers to build scalable and language-agnostic APIs.
Benefits of gRPC :
- lightweight messages : 30% smaller than equivalent JSON messages.
- automated code generation simplifies development and reduces errors.
- TLS/SSL for encrypted communications and token-based authentication.
5. RPC (Remote Procedure Call) API
RPC is an architectural style in API design that allows programs to execute procedures or functions on remote computers as if they were local calls. This is not a commonly used API type in wider organizations.
Benefits of gRPC :
- Mainly useful for developers : enables writing code as if making local function calls
5. What are some common use cases for APIs ?
APIs are everywhere!!!
Here are some real-world examples of APIs commonly used in everyday applications:
- Social Media APIs:
- Twitter API: Allows developers to create applications that interact with Twitter, such as scheduling tweets, analyzing trends, and creating chatbots for customer support.
- Instagram API: Enables businesses to connect their Instagram feeds with websites, allowing users to view comments and interactions on posts directly on the website.
- Payment APIs:
- PayPal API: Simplifies and secures online payment processes for e-commerce websites and applications.
- Mapping and Location APIs:
- Google Maps API: Allows developers to embed customizable maps into websites and applications, providing features like location-based services and real-time tracking for deliveries.
- Communication APIs:
- Warehousing APIs (each software has its own format) : Allow softwares to pass information between OMS, WMS and automated MHEs.
- Slack API: Allows for building custom bots to automate tasks and integrate Slack with other platforms.
- Development and Version Control APIs:
- GitHub API: Provides tools for developers to interact programmatically with GitHub, automating tasks like creating repositories and managing collaborators.
- Video Platform APIs:
- YouTube API: Allows embedding videos on websites, customizing video players, and extracting data for analytics purposes.
- AI and Machine Learning APIs:
- ChatGPT API: Enables developers to integrate ChatGPT’s conversational AI capabilities into various applications, such as creating customized chatbots for organizations.
- Weather APIs:
- Used by weather applications to provide real-time weather data and forecasts for specific locations.
- Travel Booking APIs:
- Used by websites like Expedia or Kayak to retrieve information about flights, hotels, and rental cars from multiple sources.
If you have prior experience with API, keep the examples close to what you have worked on. If you do not have prior experience, it will be very useful to pick a big enterprise in the industry you are interviewing for and learn more about the user cases on that, to show case your knowledge.
6. What are synchronous and asynchronous API Calls(one of the most asked questions in the interview!)?
These are two different approaches to handling communication between client applications and servers. Imagine, you send a request to a server/DB, say asking for a specific data set,
- for Synchronous calls : you will get the data set as response of your query.
- for Asynchronous calls : you get an acknowledgement first -> that a request for data set has been received. And later, you will get the data set as response for your request.
| Aspect | Synchronous API Calls | Asynchronous API Calls |
|---|---|---|
| Execution Model | Blocking, sequential | Non-blocking, parallel |
| Response Time | Immediate response | Initial acknowledgment, full response later |
| Resource Utilization | Less efficient, may tie up resources | More efficient, allows better resource management |
| Scalability | Limited in high-traffic scenarios | Better scalability, handles multiple requests simultaneously |
| Use Cases | Immediate feedback tasks (e.g., authentication) | Long-running operations, background processing |
| Implementation Complexity | Simpler to implement and debug | More complex due to callbacks and event handling |
| Performance | Slower for multiple sequential operations | Faster for concurrent operations |
| Error Handling | Straightforward, inline error handling | More complex, requires separate error handling mechanisms |
| Client Interaction | Client waits for response | Client can continue other tasks while waiting |
| Network Dependency | More sensitive to network issues | More resilient to network fluctuations |
7. How are APIs secure?
Imagine you have a house party with A-List celebrities (it doesn’t cost anything to imagine 😉 ).
API security is like protecting a special door to your house that allows trusted friends to access the party. Here’s how it works:
- Locked Door: The API is secured with strong locks (authentication) to make sure only the right people can enter.
- Guest List: Once inside, visitors (users or applications) are given specific permissions (authorization) about which rooms they can enter or what they can touch.
- Security Camera: All activities are watched and recorded (monitoring and logging) to spot any suspicious behavior.
- Bouncer: There’s a guard (API gateway) at the door checking IDs, managing how many people can enter at once, and enforcing house rules.
- Secret Language: When friends talk to each other about the party, they use a special code (encryption) so eavesdroppers can’t understand.
- House Rules: Clear guidelines (input validation) ensure visitors don’t bring in anything dangerous or unexpected.
- Regular Checkups: The house is frequently inspected and upgraded (updates and patches) to fix any weak spots or potential entry points for burglars.
By using these security measures, API owners can ensure that their “house” (data and services) remains safe while still allowing trusted visitors to access it.
8. What are API keys & OAuth tokens?
Both API Keys and OAuth tokens are used to provide access in different ways.
API Keys
API keys are unique identifiers used to authenticate and authorize access to an API. Here’s how they work:
- at registration, a unique API key – a string of randomly generated alphanumeric characters is generated.
- needs to be part of each request
- key sent is validated by API server
- once validated, access is given based on associated permissions
- Response as Access given or denied
While API keys provide a layer of security, they are generally considered less secure than other authentication methods like OAuth tokens, as they can be more easily compromised if not properly protected.
OAuth Tokens
OAuth tokens are digital credentials that enable secure, delegated access to resources without sharing passwords. Here’s how they work:
- Authorization Request: A client application requests access to user resources from an authorization server.
- User Consent: The user approves the request, typically through a consent page.
- Token Issuance: The authorization server generates and issues an access token to the client.
- Resource Access: The client uses the access token to request protected resources from the resource server.
- Validation: The resource server verifies the token and grants access if valid.
OAuth tokens come in two main types:
- Access Tokens:
- Short-lived (hours to days)
- Used for immediate resource access
- Contain information like user ID, expiration time, and access scope
- Refresh Tokens:
- Longer-lived
- Used to obtain new access tokens without user re-authentication
- Enhance security by limiting access token lifespan
| Aspect | OAuth Tokens | API Keys |
|---|---|---|
| Purpose | User-specific authentication and authorization | Application or project authentication |
| Scope | Fine-grained, can be limited to specific actions | Broad, typically full access to API |
| Lifespan | Short-lived (access tokens), renewable (refresh tokens) | Long-lived, often without expiration |
| Security | More secure, can be easily revoked | Less secure, vulnerable if compromised |
| Complexity | More complex to implement | Simpler to implement and use |
| User Context | Tied to individual users | Tied to entire application or project |
| Use Cases | Third-party integrations, user data access | Server-to-server communication, internal apps |
| Permissions | Dynamic, based on user roles and scopes | Static, based on API key permissions |
| Standard | Follows OAuth 2.0 protocol | No standardized protocol |
| User Experience | Users grant permissions via authorization flow | Developers manually manage and secure keys |
| Sample | Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c | X-API-Key: a1b2c3d4e5f6g7h8i9j0k1l2m3n4o5p6 |
9. What are API response codes?
API response codes are three-digit numbers returned by servers to indicate the outcome of an HTTP request. They provide immediate feedback on whether a request was successful, encountered an error, or requires further action.
Categories of API Response Codes
API response codes are grouped into five classes:
- 1xx (Informational): Request received, continuing process
- 2xx (Successful): Request successfully received, understood, and accepted
- 3xx (Redirection): Further action needed to complete the request
- 4xx (Client Error): Request contains bad syntax or cannot be fulfilled
- 5xx (Server Error): Server failed to fulfill a valid request
Common API Response Codes
Successful Responses (2xx)
- 200 OK: Standard response for successful HTTP requests
- 201 Created: Request fulfilled, resulting in a new resource being created
- 204 No Content: Request processed successfully, but no content to return
Client Error Responses (4xx)
- 400 Bad Request: Server cannot process the request due to client error
- 401 Unauthorized: Authentication is required and has failed or not been provided
- 403 Forbidden: Server understood the request but refuses to authorize it
- 404 Not Found: Requested resource can not be found
Server Error Responses (5xx)
- 500 Internal Server Error: Generic error message when server encounters an unexpected condition
- 503 Service Unavailable: Server is not ready to handle the request
API response codes are crucial for developers to understand the status of their requests and to implement proper error handling in their applications.
10. Share details of the project you worked on with APIs?
This is your moment to shine ❤ , not that you know the basics of APIs ! Take all of the information above and share more about the project you worked on previously :
- What was the project scope in entirety ? Example : A project to integrate in house software with a third part software…
- What was your role in the project ? Example : As a business analyst, your key responsibility was …
- What were the challenges you faced in the project ? Example : Operations resistance to change … , stakeholder buy in … , personal learning curve…
- Cover the scope by activities you were part of : Ideate , Design, Develop, Test, Train, Deploy …
- Share statistical details : budget , timeline etc …
Let the interviewer drive the conversation, but more or less, above is what you’ll be asked. Again, if you are not aware of any concepts, accept that you don’t know :). That’s completely OK!





